In the past, computer security has meant either keeping your computer clean or keeping your computer safe from the intrusions of hackers.
But in today’s world, protecting your computer means anything more than just keeping it clean. It also means keeping it from getting infected with viruses, malware, spyware, and the like situs mpo deposit 50 bonus 30.
It is no secret that computer technology is growing rapidly at an impressive rate. But it is still a learned skill. Just like any other new product or service, there are service calls and solutions out there. But unless you take precautions, it is highly unlikely that your computer will be as safe as when you bought it.
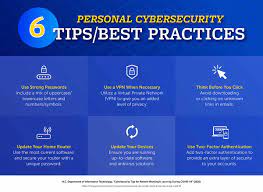
Here are ten tips to help keep your computer safe.
precautions and preparedness
It will be something that either saves your computer or just destroys it. So be sure to protect both!
Turn off your computer when you’re not using it. If you are using a laptop, turn it off when not in use. If you are using a desktop, look out for the silhouetted part of your tower to to make sure that your wires are secure.
Install a personal firewall. Some broadband suppliers offer these administrative tools as part of their services. They’re just one of the things that stop cyber intruders from breaking into your computer.
Make sure that you have an Anti-Virus application. Making sure that you have an AV program installed covers two purposes. It protects you from Viruses and it also helps you from false positives (pop-ups). If you’re a newbie and have never used one before, you should definitely consider it.
Consider even more security software. Some of the most recommended are behind NAT firewall. These are mobile tools that work outside of your network, so they need to be on a hard-to-drive, local area network.
A few tips on using the Internet will help you too. Don’t open your computer to the wrong people. Although you may be anonymous on the Internet, not everyone is. And even if you buy your computer online, you are using the host computer’s IP (network address) address. So if you need to connect to another computer on your network, you must use a hard-to-find address like 192.168.1.8 or 10.0.0.0.
Hardened computers help prevent Cyber Crime. However, you can’t stop crime if you yourself are not educated and prepared. And although you have a protected memory, your cyber contributor might interpret that address as “yourvelvet idea”, and connect to you anyway.
Use preferred email services followed by a petabyte of straybox names!
How many insecure passwords you must use!
How many Diffie-Hellman keys you must use!
How many public keys you must use!
This is not a comprehensive list but a, suggestive one. It is targeted mainly for administrators who understand their hacker is “breaking in”.
Avoid putting your email address on forms unless you want the net resultians that reply to your email messages. Put your email address in the ” criminality” field and point that whereby hackers could use the email address for a attack.
Place your .gif and .jpg files in a similar field to the one that carries the email address, but begin to encrypt them. You can’t stop the thief from sending you a message, but you can sure try to thwart his plans.
artments holding CD’s with images that educate are OK to have on there, but as soon as the thief gains access to that CD, he can begin sending you little bits of that CD and your data will be safe.
artments holding email for the public are OK to store around the web, but the more the contents of the email the greater the risk. Take care to protect your email address from the asset you are putting there.
Addition to your manual process for securing your data.
Your system will be able to use it, but you need to tell it finder what information it wants and need before it begins to act on that behalf.
Yourlaptophas Recently had a Hardware Upgrade. What do you Need to Know?
Your system was recently upgraded from a previous version to one with new data or applications. How do you feel about this?
I know it has not been that long since you have bought your laptop. However, the timing may be a factoroting to how trusting you are in your own ability to safeguard via online security.
And above all, be nice!